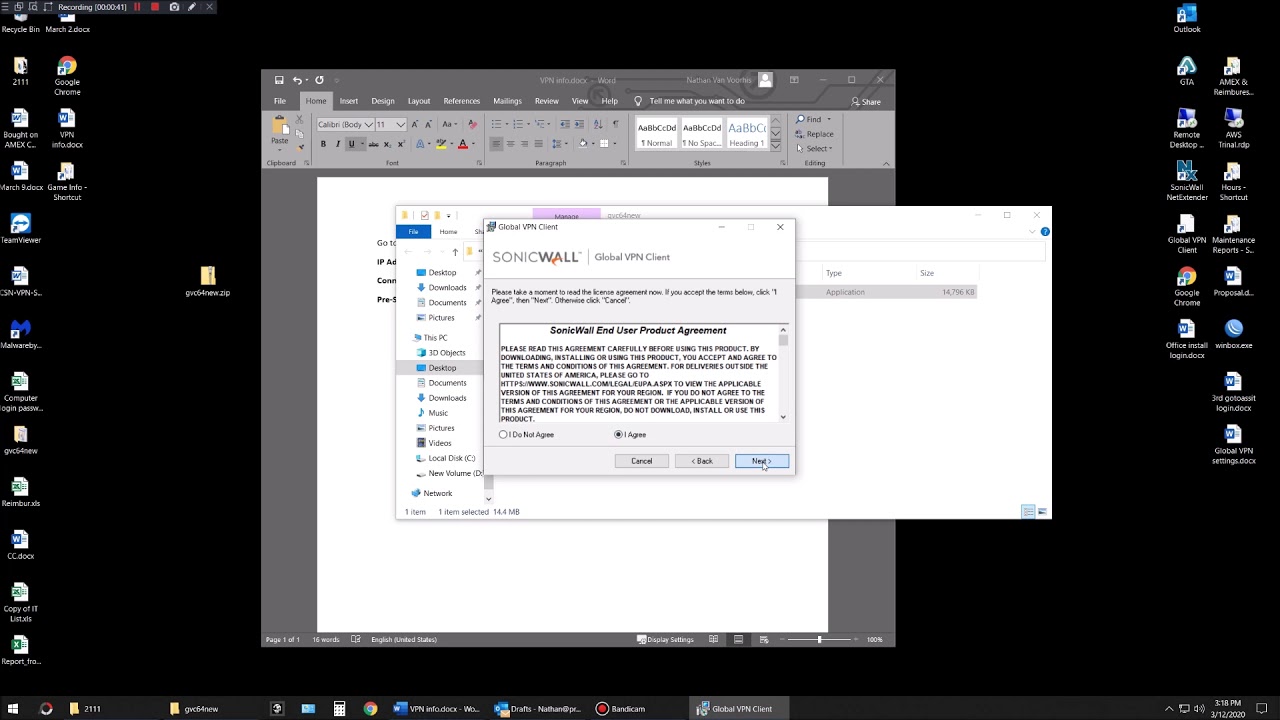
Sonicwall Global Vpn Mac
Posted By admin On 23.04.21

If you searching to test Download Sonicwall Global Vpn Client Mac And Free Secure Vpn For Mac price. SonicWall Mobile Connect™ provides users full network-level access to corporate and academic resources over encrypted SSL VPN connections. The client provides anytime, anywhere access to critical applications such as email, virtual desktop sessions and other macOS applications. SonicWall Global VPN on a Mac? Ask Question Asked 5 years, 2 months ago. Viewed 5k times 0. I use the SonicWall Gobal VPN Client on Windows to connect.
- Sonicwall Global Vpn Client For Mac
- Sonicwall Global Vpn Client Mac Address
- Install Sonicwall Global Vpn Client
- Sonicwall Global Vpn Client Change Mac Address
- Sonicwall Global Vpn For Mac
Configuring GroupVPN Policies
GroupVPN policies facilitate the set up and deployment of multiple Global VPN Clients by the firewall administrator. GroupVPN is only available for Global VPN Clients and it is recommended you use XAUTH/RADIUS or third party certificates in conjunction with the Group VPN for added security.
From the Network > Zones page, you can create GroupVPN policies for any zones. SonicOS provides two default GroupVPN policies for the WAN and WLAN zones, as these are generally the less trusted zones. These two default GroupVPN policies are listed in the VPN Policies panel on the VPN > Settings page:
In the VPN Policy dialog, from the Authentication Method menu, you can choose either the IKE using Preshared Secret option or the IKE using 3rd Party Certificates option for your IPsec Keying Mode.
Types of Group VPN/Global VPN Client Scenarios and Configurations?: https://support.software.dell.com/kb/sw7411
Troubleshooting Group VPN/Global VPN Client related Issues: https://support.software.dell.com/kb/sw7569
Topics:
Configuring GroupVPN with IKE using Preshared Secret on the WAN Zone
Configuring GroupVPN with IKE using 3rd Party Certificates
Configuring GroupVPN with IKE using Preshared Secret on the WAN Zone
Click the Editicon for the WAN GroupVPN entry. The VPN Policy dialog is displayed.
In the Generaltab,IKE using Preshared Secretis the default setting for Authentication Method.
A Shared Secret is automatically generated by the firewall in the Shared Secret field. You can generate your own shared secret. Shared Secrets must be a minimum of four characters.
Click the Proposals tab to continue the configuration process.
In the IKE (Phase 1) Proposal section, use the following settings:
Select the DH Group from the DH Group drop-down menu:
Group 1, Group 2 (default), Group 5, or Group 14 – Select Group 2 from the DH Group drop-down menu.
Select DES, 3DES (default), AES-128, AES-192, or AES-256 from the Encryption drop-down menu.
Select the desired authentication method from the Authentication drop-down menu: MD5, SHA1 (default), SHA256, SHA384, or SHA512.
Enter a value in the Life Time (seconds) field. The default setting of 28800 forces the tunnel to renegotiate and exchange keys every 8 hours.
In theIPsec (Phase 2) Proposal section, select the following settings:
Select the desired protocol from the Protocol drop-down menu. Currently, ESP is the only option.
Select 3DES (default), AES-128, AES-192, or AES-256 from the Encryption drop-down menu.
Select the desired authentication method from the Authentication drop-down menu: MD5, SHA1 (default), SHA256, SHA384, SHA512, AES-XCBX, or None.
Select Enable Perfect Forward Secrecy if you want an additional Diffie-Hellman key exchange as an added layer of security.
Enter a value in the Life Time (seconds) field. The default setting of 28800 forces the tunnel to renegotiate and exchange keys every 8 hours.
Advanced Settings
Disable IPsec Anti-Replay - Stops packets with duplicate sequence numbers from being dropped.
Enable Windows Networking (NetBIOS) broadcast - Allows access to remote network resources by browsing the Windows® Network Neighborhood.
Enable Multicast - Enables IP multicasting traffic, such as streaming audio (including VoIP) and video applications, to pass through the VPN tunnel.
Accept Multiple Proposals for Clients - Allows multiple proposals for clients, such as the IKE (Phase 1) Proposal or the IKE (Phase 2) Proposal, to be accepted.
Management via this SA: - If using the VPN policy to manage the firewall, select the management method, either HTTP, SSH, or HTTPS.
Default Gateway- Allows you to specify the IP address of the default network route for incoming IPsec packets for this VPN policy. Incoming packets are decoded by the firewall and compared to static routes configured in the firewall.
Client Authentication
Require Authentication of VPN Clients via XAUTH - Requires that all inbound traffic on this VPN tunnel is from an authenticated user. Unauthenticated traffic is not allowed on the VPN tunnel. The Trusted users group is selected by default. You can select another user group or Everyone from User Group for XAUTH users from the User group for XAUTH users menu.
Allow Unauthenticated VPN Client Access - Allows you to enable unauthenticated VPN client access. If you clear Require Authentication of VPN Clients via XAUTH, the Allow Unauthenticated VPN Client Access menu is activated. Select an Address Object or Address Group from menu of predefined options, or select Create new address object or Create new address group to create a new one.
Click the Client tab, select any of the following settings you want to apply to your GroupVPN policy.
User Name and Password Caching
Cache XAUTH User Name and Password on Client - Allows the Global VPN Client to cache the user name and password.
Never - Global VPN Client is not allowed to cache the username and password. The user will be prompted for a username and password when the connection is enabled, and also every time there is an IKE Phase 1 rekey.
Single Session - Global VPN Client user prompted for username and password each time the connection is enabled and will be valid until the connection is disabled. The username and password is used through IKE Phase 1 rekey.
Always - Global VPN Client user prompted for username and password only once when connection is enabled. When prompted, the user will be given the option of caching the username and password.
Client Connections
Virtual Adapter Settings - The use of the Virtual Adapter by the Global VPN Client (GVC) is dependent upon a DHCP server, either the internal SonicOS or a specified external DHCP server, to allocate addresses to the Virtual Adapter.
None - A Virtual Adapter will not be used by this GroupVPN connection.
DHCP Lease - The Virtual Adapter will obtain its IP configuration from the DHCP Server only, as configure in the VPN > DHCP over VPN page.
DHCP Lease or Manual Configuration - When the GVC connects to the firewall, the policy from the firewall instructs the GVC to use a Virtual Adapter, but the DHCP messages are suppressed if the Virtual Adapter has been manually configured. The configured value is recorded by the firewall so that it can proxy ARP for the manually assigned IP address. By design, there are currently no limitations on IP address assignments for the Virtual Adapter. Only duplicate static addresses are not permitted.
Allow Connections to - Client network traffic matching destination networks of each gateway is sent through the VPN tunnel of that specific gateway.
This Gateway Only - Allows a single connection to be enabled at a time. Traffic that matches the destination networks as specified in the policy of the gateway is sent through the VPN tunnel. If this option is selected along with Set Default Route as this Gateway, then the Internet traffic is also sent through the VPN tunnel. If this option is selected without selecting Set Default Route as this Gateway, then the Internet traffic is blocked.
All Secured Gateways - Allows one or more connections to be enabled at the same time. Traffic matching the destination networks of each gateway is sent through the VPN tunnel of that specific gateway. If this option is selected along with Set Default Route as this Gateway, then Internet traffic is also sent through the VPN tunnel. If this option is selected without Set Default Route as this Gateway, then the Internet traffic is blocked. Only one of the multiple gateways can have Set Default Route as this Gateway enabled.
Split Tunnels - Allows the VPN user to have both local Internet connectivity and VPN connectivity.
Set Default Route as this Gateway - Enable this check box if all remote VPN connections access the Internet through this VPN tunnel. You can only configure one VPN policy to use this setting.
Client Initial Provisioning
Use Default Key for Simple Client Provisioning- Uses Aggressive mode for the initial exchange with the gateway and VPN clients uses a default Preshared Key for authentication.
Configuring GroupVPN with IKE using 3rd Party Certificates
To configure GroupVPN with IKE using 3rd Party Certificates, follow these steps:
In the VPN > Settings page click the Edit icon under Configure. The VPN Policy window is displayed.
In the Security Policysection, select IKE using 3rd Party Certificates from the Authentication Method drop-down menu.
Select a certificate for the firewall from the Gateway Certificate menu.
Select one of the following Peer ID types from the Peer ID Type menu:
Distinguished Name - This is based on the certificate’s Subject Distinguished Name field, which is contained in all certificates by default.
The format of any Subject Distinguished Name is determined by the issuing Certificate Authority. Common fields are Country (C=), Organization (O=), Organizational Unit (OU=), Common Name (CN=), Locality (L=), and vary with the issuing Certificate Authority. The actual Subject Distinguished Name field in an X.509 Certificate is a binary object which must be converted to a string for matching purposes. The fields are separated by the forward slash character, for example: /C=US/O=SonicWALL, Inc./OU=TechPubs/CN=Joe Pub.
Up to three organizational units can be specified. The usage is c=*;o=*;ou=*;ou=*;ou=*;cn=*. The final entry does not need to contain a semi-colon. You must enter at least one entry, for example, c=us.
Email ID and Domain Name (default) - Both the Email ID and Domain Name types are based on the certificate's Subject Alternative Name field, which is not contained in all certificates by default. If the certificate does not contain a Subject Alternative Name field, this filter does not work.
The Email ID and Domain Name filters can contain a string or partial string identifying the acceptable range required. The strings entered are not case sensitive and can contain the wild card characters * (for more than 1 character) and ? (for a single character). For example, the string *@sonicwall.com when Email ID is selected allows anyone with an email address that ended in sonicwall.com to have access; the string *sv.us.sonicwall.com when Domain Name is selected allows anyone with a domain name that ended in sv.us.sonicwall.com to have access.
Sonicwall Global Vpn Client For Mac
Enter the Peer ID filter in the Peer ID Filter field.
Check Allow Only Peer Certificates Signed by Gateway Issuer to specify that peer certificates must be signed by the issuer specified in the Gateway Certificate menu.
In the IKE (Phase 1) Proposal section, select the following settings:
Group 1, Group 2, Group 5, or Group 14
Select 3DES (default), AES-128, AES-192, or AES-256 from the Encryption menu.
Select the desired authentication method from the Authentication menu: MD5, SHA1 (default), SHA256, SHA384, SHA512, AES-XCBX, or None.
Enter a value in the Life Time (seconds) field. The default setting of 28800 forces the tunnel to renegotiate and exchange keys every 8 hours.
In theIPsec (Phase 2) Proposal section, select the following settings:
Select the desired protocol from the Protocol menu. Currently, ESP is the only option.
Select 3DES (default), AES-128, AES-192, or AES-256 from the Encryption drop-down menu.
Select the desired authentication method from the Authentication drop-down menu: MD5, SHA1 (default), SHA256, SHA384, SHA512, AES-XCBX, or None.
Select Enable Perfect Forward Secrecy if you want an additional Diffie-Hellman key exchange as an added layer of security.
Enter a value in the Life Time (seconds) field. The default setting of 28800 forces the tunnel to renegotiate and exchange keys every 8 hours.
Click on the Advanced tab and select any of the following optional settings that you want to apply to your GroupVPN Policy:
Enable Windows Networking (NetBIOS) broadcast - Allows access to remote network resources by browsing the Windows Network Neighborhood.
Enable Multicast - Enables IP multicasting traffic, such as streaming audio (including VoIP) and video applications, to pass through the VPN tunnel.
Management via this SA - If using the VPN policy to manage the firewall, select the management method, either HTTP, SSH, or HTTPS.
Sonicwall Global Vpn Client Mac Address
Default Gateway - Used at a central site in conjunction with a remote site using the Route all Internet traffic through this SA check box. Default LAN Gateway allows you to specify the IP address of the default LAN route for incoming IPsec packets for this SA.
Enable OCSP Checking and OCSP Responder URL - Enables use of Online Certificate Status Protocol (OCSP) to check VPN certificate status and specifies the URL where to check certificate status. See Using OCSP with Dell SonicWALL Network Security Appliances.
Require Authentication of VPN Clients via XAUTH - Requires that all inbound traffic on this VPN policy is from an authenticated user. Unauthenticated traffic is not allowed on the VPN tunnel.
User group for XAUTH users - Allows you to select a defined user group for authentication.
Allow Unauthenticated VPN Client Access - Allows you to specify network segments for unauthenticated Global VPN Client access.
Click on the Client tab and select any of the following boxes that you want to apply to Global VPN Client provisioning:
Cache XAUTH User Name and Password - Allows the Global VPN Client to cache the user name and password. Select from:
Never - Global VPN Client is not allowed to cache username and password. The user will be prompted for a username and password when the connection is enabled and also every time there is an IKE phase 1 rekey.
Single Session - The user will be prompted for username and password each time the connection is enabled and will be valid until the connection is disabled. This username and password is used through IKE phase 1 rekey.
Always - The user will be prompted for username and password only once when connection is enabled. When prompted, the user will be given the option of caching the username and password.
Virtual Adapter Settings - The use of the Virtual Adapter by the Global VPN Client (GVC) is dependent upon a DHCP server, either the internal SonicOS or a specified external DHCP server, to allocate addresses to the Virtual Adapter.
None - A Virtual Adapter will not be used by this GroupVPN connection.
DHCP Lease - The Virtual Adapter will obtain its IP configuration from the DHCP Server only, as configure in the VPN > DHCP over VPN page.
DHCP Lease or Manual Configuration - When the GVC connects to the firewall, the policy from the firewall instructs the GVC to use a Virtual Adapter, but the DHCP messages are suppressed if the Virtual Adapter has been manually configured. The configured value is recorded by the firewall so that it can proxy ARP for the manually assigned IP address. By design, there are currently no limitations on IP address assignments for the Virtual Adapter. Only duplicate static addresses are not permitted.
Allow Connections to - Client network traffic matching destination networks of each gateway is sent through the VPN tunnel of that specific gateway.
This Gateway Only - Allows a single connection to be enabled at a time. Traffic that matches the destination networks as specified in the policy of the gateway is sent through the VPN tunnel. If this option is selected along with Set Default Route as this Gateway, then the Internet traffic is also sent through the VPN tunnel. If this option is selected without selecting Set Default Route as this Gateway, then the Internet traffic is blocked.
All Secured Gateways - Allows one or more connections to be enabled at the same time. Traffic matching the destination networks of each gateway is sent through the VPN tunnel of that specific gateway.
If this option is selected along with Set Default Route as this Gateway, then Internet traffic is also sent through the VPN tunnel. If this option is selected without Set Default Route as this Gateway, then the Internet traffic is blocked.
Split Tunnels - Allows the VPN user to have both local Internet connectivity and VPN connectivity.
Set Default Route as this Gateway - Enable this check box if all remote VPN connections access the Internet through this SA. You can only configure one SA to use this setting.
Use Default Key for Simple Client Provisioning- Uses Aggressive mode for the initial exchange with the gateway and VPN clients uses a default Preshared Key for authentication.
Exporting a VPN Client Policy
Click the Export icon in the Configure column for the GroupVPN entry in the VPN Policies table. The Export VPN Client Policy window appears.
rcf format is required for SonicWALL Global VPN Clients is selected by default. Files saved in the rcf format can be password encrypted. The firewall provides a default file name for the configuration file, which you can change.
Click Yes. The VPN Policy Export window appears.
Select a VPN Access Networks from the Select the client Access Network(s) you wish to export drop-down menu.
Type a password in the Password field and reenter it in the Confirm Password field, if you want to encrypt the exported file. If you choose not to enter a password, the exported file is not encrypted.
Click Submit. If you did not enter a password, a message appears confirming your choice.
Click OK. You can change the configuration file before saving.
Click Close.
Businesses large and small need to address the growing demands of more distributed work sites and an increasingly mobile workforce in order to compete in today’s global marketplace. Remote access has become a business imperative.
SonicWall VPN Clients offer a flexible easy-to-use, easy-to-manage Virtual Private Network (VPN) solution that provides distributed and mobile users with secure, reliable remote access to corporate assets via broadband, wireless and dial-up connections. For remote client-to-host secure access, SonicWall offers both SSL VPN and IPSec VPN connectivity options. For SSL VPN, SonicWall NetExtender provides thin client connectivity and clientless Web-based remote access for Windows, Windows Mobile, Mac and Linux-based systems. For IPSec VPN, SonicWall Global VPN Client enables the client system to download the VPN client for a more traditional client-based VPN experience.
- Enhanced layered security
- Easy VPN management
- Ease-to-follow wizards
- Extended user reach and productivity
- VPN session reliability
- Clientless connectivity
- NetExtender technology
- Mobile device support
Install Sonicwall Global Vpn Client
SonicWall Global VPN Client
- Easy-to-follow wizards help users install and configure a VPN connection quickly and easily. IPSec VPN users simply enter the domain name or IP address of the SonicWall VPN gateway and the Global VPN Client configuration policy is automatically downloaded.
- Extended user reach and productivity by connecting from any single or dualprocessor computer running one of a broad range of Microsoft® Windows® platforms. Further extending secure remote access, the Global VPN Client enables encapsulated VPN traffic to traverse any IP network using Network Address Translation (NAT).
- VPN session reliability provides simultaneous Global VPN Client connections that can be established to multiple SonicWall VPN gateways. The Global VPN Client supports redundant SonicWall VPN gateways to ensure mission-critical network access in the event the primary gateway fails.
SonicWall SSL VPN
- NetExtender - Clientless connectivity removes the need for a pre-installed or “fat” VPN client, thus freeing administrators from the tedious and costly task of installing and updating a client on users’ Windows, Mac or Linux-based systems.
- NetExtender technology provides enhanced capabilities such as network level access to additional resources, services and applications on the corporate network.
- Mobile device support to access an entire intranet as well as Web-based applications provides greater flexibility for a remote workforce.
Time is of the essence; SonicWall is offering, for a limited time, the following Work-From-Home Securely special offers to help you keep your customers safe and operational:
- SonicWall NSA 2650 '3 & Free' Promotion
- Free Upgrade your current SonicWall NSA firewall to an NSA 2650 at no additional charge with the purchase of a three-year subscription of the SonicWall Advanced Gateway Security Suite.
Sonicwall Global Vpn Client Change Mac Address
Shop our top SonicWall's remote access solutions to make working from home safe and easy.
Sonicwall Global Vpn For Mac





